Bluetooth Hacking Ppt
New bluetooth hack affects millions of devices from major vendors.
The attack carried out by exploiting bluetooth's electronic business card feature as a message carrier. the hacker cannot access any information or intercept messages. you can protect yourself from these unsolicited spam messages by putting your bluetooth settings into "invisible," or "non-discoverable", mode. Bluetooth hacking 1. seminar on blue tooth hacking [security and threats] bydhanashree waikar roll no 3379 project guide prof. n. r. talhar. Keywords: bluetooth hacking, mobile phone hacking, wireless hacking abstract this paper describes a student project examining mechanisms with which to attack bluetooth-enabled devices. the paper briefly describes the protocol architecture of bluetooth and the java interface that programmers can use to connect to bluetooth communication services.
Jan 29, 2010 · bluetooth hacking 1. bluetooth hacking ppt seminar on blue tooth hacking [security and threats] bydhanashree waikar roll no 3379 project guide prof. n. r. talhar.

Certified ethical hacker (ceh) students and licensed penetration testers (lpts) should develop a solid understanding of these common methods for hacking bluetooth technology. if malicious hackers can find a way to infiltrate company networks via bluetooth, ethical hackers should know how to as well in order to prevent such vulnerable entry points. Given that the bluetooth has been used for a long time, there exist several flaws in the system. these flaws have been subject to different types of attacks over time, vulnerable to hacking. which makes the technology very. types of bluetooth hacking: bluejacking. the first most popular attack on bluetooth enables devices is bluejacking. Bluetooth seminar and ppt with pdf report: bluetooth provides short-range, wireless connectivity between electronic devices. there are many types of bluetooth devices such as head set, in-car bluetooth system, bluetooth equipped printer, bluetooth equipped web cam, bluetooth gps system and bluetooth key board. this page contains bluetooth seminar and ppt with pdf report. Bluetooth hacking full disclosure @ 21c3 hacking bluetooth enabled mobile phones and beyond full disclosure 21c3: the usual suspects 21st chaos communication congress december 27th to 29th, 2004 berliner congress center, berlin, germany adam laurie marcel holtmann martin herfurt.
Bluetooth seminar ppt with pdf report. advantages of bluetooth. eliminates wires; facilitates data and voice communication; offers formation of ad hoc networks; standardized protocol; free of charge; easy to use; low power consumes battery less; stationary and mobile environments; disadvantages of bluetooth. data sent between two bluetooth devices is very slow compared with wi-fi transfer rate. security is biggest disadvantage as transfer takes place through radio waves and a hacker can. Jul 03, 2014 · bluejacking is probably the most common bluetooth hacking ppt form of bluetooth hacking. this happens when a hacker searches for discoverable devices in the area and then sends spam in the form of text messages to the devices. this form of hacking is rather childish and harmless. Running at commands via bluetooth it is required to pair the peripheral device (speakers, headsets, etc. ) with the targeted smartphone, establishing a communication channel. when receiving an at command the system-level bluetooth component of the device recognizes the command with the prefix “at” and contrasts it with a list of legitimate.
Bluetooth Hacking Linkedin Slideshare
A recent research published by vulnerability testing specialists from purdue university details a new exploit that abuses some android operating system smartphones through the use of malicious peripheral devices (specifically through bluetooth and usb). Sep 20, 2014 · bluetooth based devices (application) : • bluetooth in electronics 16. application (contd…) •bluetooth in medical devices with the help of these divices various data can be collected and can be sent directly to the computer to keep a daily track of patients heart beat,blood sugar levels etc. When bluetooth is activated, hackers take control of the device(s) and spread malware that goes completely unnoticed by the user. additionally, once an infected device comes within range of other bluetooth enabled systems, the virus can spread from one user to another. Jul 24, 2018 · the bluetooth hacking vulnerability, tracked as cve-2018-5383, affects firmware or operating system software drivers from some major vendors including apple, broadcom, intel, and qualcomm, while the implication of the bug on google, android and linux are still unknown.

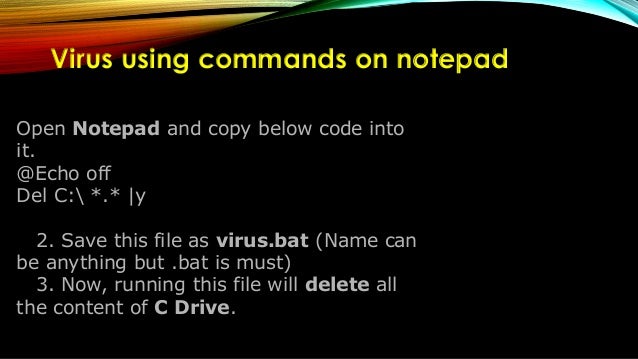
Bluetooth has design and used for short distance communication, it is an open wireless protocol and operate on the frequency of 2. 4 ghz. now a days mobile phones, laptops and pda devices has a built in bluetooth option to use. it can bluetooth hacking ppt use over a range of 10 meter. now as you know if there Bluetooth hacking. uses logical link control and adaptation-layer protocol (l2cap) to communicate over rf (l2cap is data link layer). synchronous connection-oriented (sco) it has to get there, and quickly. asynchronous connection-less (acl) meh, whenever dude. security is based around the concept of bonding, and pairing is how you create a bond.
Bluetooth Vulnerability Could Expose Device Data To
The bluetooth flaw allows hackers to force a pair of bluetooth devices to use weaker encryption, making it far easier to crack. hackers could then snoop on communications or take over a device. Billions of bluetooth devices could get hit by this attack. bluetooth hacking ppt more than 5 billion devices are vulnerable to a "highly infectious" malware attack. go ahead, blame the internet of things. Bluetooth vulnerabilities abound. at first glance, it might seem like it’s pretty risky to use bluetooth. at the recent def con 27 security conference, attendees were advised to disable bluetooth on their devices while they were there. of course, it makes sense you’d want to be more careful with your device security if you’re surrounded by thousands of hackers in a fairly small venue.
1. super bluetooth hack 1. 08. this software is used for controlling and reading information from remote phone via bluetooth or infra. phone list and sms can be stored in html format. Jun 09, 2017 · updates to the phone's firmware and new security measures have made carrying out these attacks very difficult for hackers. most hacking requires expensive software and hardware, making it unlikely that the average person’s device will be the target of an attack. (learn about bluetooth 4. 0 in from bluetooth to new tooth: a look at bluetooth 4. 0. ).
One common approach to hacking bluetooth devices is to employ malformed objects, which are legal files exchanged between bt devices that contain invalid information, thus causing unexpected results. when a bluetooth device receives a malformed object, such as a vcard or vcal file, the device may become unstable or fail completely. Bluetooth is the technology that allows electronic devices like smartphones, tablets, portable speakers, digital assistants, wearable fitness trackers and home security equipment to wirelessly connect to each other through a network. bluetooth is everywhere. in 2018, it was predicted that almost 4 billion bluetooth devices would be shipped. the. bluetooth hacking ppt Bluejacking is probably the most common form of bluetooth hacking. this happens when a hacker searches for discoverable devices in the area and then sends spam in the form of text messages to the devices. this form of hacking is rather childish and harmless. it was once used mainly to prank people in the past when mobile devices came with bluetooth that was automatically set to discoverable.
A recent research published by vulnerability testing specialists from purdue university details a new exploit that abuses some android operating system smartphones through the use of malicious peripheral devices (specifically through bluetooth and usb).. the application processor of almost any relatively recent smartphone model uses the at command interface to launch high-level commands to the. Aug 16, 2019 · the bluetooth flaw allows hackers to force a pair of bluetooth devices to use weaker encryption, making it far easier to crack. hackers could then snoop on communications or take over a device.
Komentar
Posting Komentar